Remote SSH access to IoT devices behind a firewall has become increasingly important as more businesses and individuals integrate IoT technology into their daily operations. This guide explores how to securely connect to IoT devices using SSH on Ubuntu while navigating the complexities of firewalls and network restrictions.
As the Internet of Things (IoT) continues to expand, the need for secure and efficient remote access solutions grows. Whether you're a developer, network administrator, or hobbyist, understanding how to establish remote SSH connections to IoT devices behind firewalls is a critical skill. This article provides a step-by-step approach to setting up and maintaining these connections using Ubuntu.
By the end of this guide, you'll have a clear understanding of the tools, techniques, and best practices necessary to securely access IoT devices remotely. We'll cover everything from basic configurations to advanced security measures, ensuring your network remains protected while maintaining accessibility.
Read also:Hdhub4u Hindi Movies Your Ultimate Guide To Stream And Download Highquality Films
Table of Contents
- Introduction to SSH
- Understanding Firewalls
- IoT and SSH: A Perfect Match
- Setting Up SSH on Ubuntu
- Configuring Port Forwarding
- Using Reverse SSH Tunneling
- Security Best Practices
- Tools and Software Recommendations
- Troubleshooting Common Issues
- Conclusion and Next Steps
Introduction to SSH
Secure Shell (SSH) is a cryptographic network protocol designed to provide secure communication over an unsecured network. It is widely used for remote command-line login and other secure network services. SSH ensures data integrity, confidentiality, and authentication, making it an ideal choice for accessing IoT devices remotely.
Why Use SSH for IoT Devices?
- SSH encrypts all data transmitted between your local machine and the IoT device.
- It supports key-based authentication, reducing the risk of brute-force attacks.
- SSH is platform-independent, allowing seamless integration with various operating systems, including Ubuntu.
When working with IoT devices behind firewalls, SSH provides a reliable and secure method for remote access. This section lays the groundwork for understanding how SSH can be utilized effectively in such scenarios.
Understanding Firewalls
A firewall is a network security system that monitors and controls incoming and outgoing network traffic based on predetermined security rules. Firewalls act as a barrier between trusted internal networks and untrusted external networks, such as the internet.
Types of Firewalls
- Packet Filtering Firewalls: Examine individual packets and allow or deny them based on predefined rules.
- Stateful Inspection Firewalls: Monitor active connections and make decisions based on context.
- Application-Level Gateways: Operate at the application layer, providing advanced filtering capabilities.
Understanding the type of firewall protecting your IoT device is crucial for configuring remote SSH access. This knowledge helps in implementing appropriate strategies, such as port forwarding or reverse SSH tunneling, to bypass firewall restrictions.
IoT and SSH: A Perfect Match
The integration of SSH with IoT devices offers numerous advantages. By leveraging SSH, you can securely manage and monitor IoT devices from anywhere in the world. This section explores the benefits of using SSH for IoT applications and provides real-world examples.
Read also:Vegamoviesin Your Ultimate Destination For Movie Entertainment
Benefits of SSH for IoT
- Enhanced Security: Protect sensitive data and prevent unauthorized access.
- Remote Administration: Easily manage IoT devices without physical presence.
- Scalability: SSH can handle multiple devices, making it suitable for large-scale IoT deployments.
For instance, imagine a smart home system where multiple IoT devices are connected to a central hub running Ubuntu. Using SSH, you can remotely configure and troubleshoot these devices, ensuring optimal performance and security.
Setting Up SSH on Ubuntu
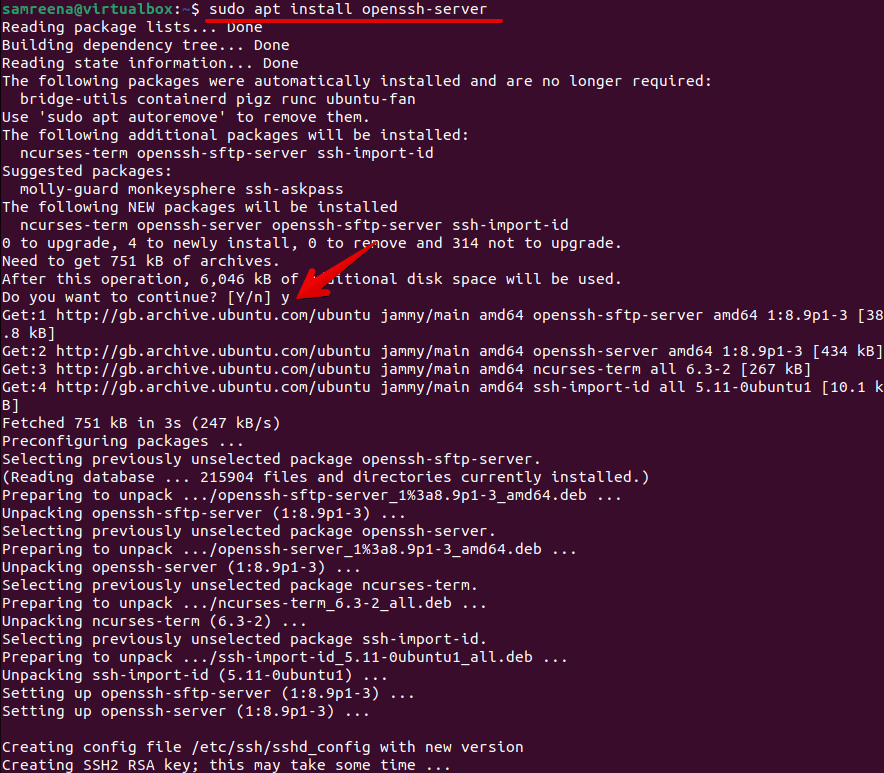
Ubuntu is a popular Linux distribution widely used for IoT applications due to its stability and ease of use. Setting up SSH on Ubuntu involves installing the OpenSSH server and configuring basic settings.
Installing OpenSSH Server
Begin by updating your system and installing the OpenSSH server:
sudo apt update && sudo apt install openssh-server
Configuring SSH Settings
After installation, edit the SSH configuration file to customize settings:
sudo nano /etc/ssh/sshd_config
Some essential configurations include:
- Changing the default SSH port to enhance security.
- Disabling root login to prevent unauthorized access.
- Enabling key-based authentication for added security.
Configuring Port Forwarding
Port forwarding is a technique used to redirect communication requests from one address and port number combination to another while maintaining the same protocol. This method allows you to access IoT devices behind firewalls by forwarding specific ports to the target device.
Steps to Configure Port Forwarding
- Log in to your router's admin interface.
- Navigate to the port forwarding or virtual server settings.
- Add a new rule, specifying the external port, internal IP address, and internal port.
- Save the settings and test the connection.
Port forwarding is a straightforward method for bypassing firewalls, but it requires careful configuration to ensure security.
Using Reverse SSH Tunneling
Reverse SSH tunneling is an alternative method for accessing IoT devices behind firewalls. This technique involves creating a secure tunnel from the IoT device to a server with a public IP address, allowing remote access without modifying firewall settings.
How Reverse SSH Tunneling Works
The process involves the following steps:
- Set up a server with a static IP address.
- Configure the IoT device to establish a reverse SSH tunnel to the server.
- Access the IoT device through the server using the established tunnel.
This method is particularly useful when dealing with strict firewall policies that restrict incoming connections.
Security Best Practices
When working with remote SSH connections, implementing robust security measures is essential to protect your IoT devices and network. This section outlines key best practices for securing SSH access.
Key Security Measures
- Use strong, unique passwords or passphrase-protected SSH keys.
- Enable two-factor authentication (2FA) for added security.
- Regularly update your system and software to patch vulnerabilities.
- Monitor connection logs for suspicious activity.
By adhering to these best practices, you can significantly reduce the risk of unauthorized access and ensure the security of your IoT devices.
Tools and Software Recommendations
Several tools and software can enhance your remote SSH experience when working with IoT devices behind firewalls. This section highlights some popular options and their features.
Recommended Tools
- SSHFS: Allows you to mount remote file systems over SSH.
- mosh (mobile shell): Provides a more reliable connection compared to traditional SSH.
- Fail2Ban: Prevents brute-force attacks by banning IP addresses after multiple failed login attempts.
These tools can streamline your workflow and improve the efficiency of managing IoT devices remotely.
Troubleshooting Common Issues
Despite careful planning and configuration, issues may arise when setting up remote SSH access to IoT devices behind firewalls. This section addresses common problems and provides solutions.
Common Issues and Solutions
- Connection Timeout: Ensure the correct IP address and port are used, and check firewall rules.
- Authentication Failure: Verify SSH keys and passwords, and ensure proper permissions are set.
- Network Connectivity Problems: Test network settings and ensure the IoT device is connected to the internet.
By identifying and resolving these issues promptly, you can maintain uninterrupted access to your IoT devices.
Conclusion and Next Steps
In conclusion, remote SSH access to IoT devices behind firewalls is a powerful tool for managing and monitoring IoT systems effectively. By following the steps outlined in this guide, you can securely connect to your IoT devices using SSH on Ubuntu while adhering to best practices and maintaining network security.
We encourage you to experiment with the techniques discussed and explore additional tools and resources to enhance your remote access capabilities. Don't forget to share your experiences and insights in the comments section below. For more in-depth guides and tutorials, explore our other articles and stay updated on the latest developments in IoT technology.